Notizie
Subscribe to our newsletter to receive the same news by email:
Changes and updates
Update Tor Browser to 15.0.7.
Simplify the home page of Tor Browser.
Update the Tor client to 0.4.9.5.
Update Thunderbird to 140.7.1.
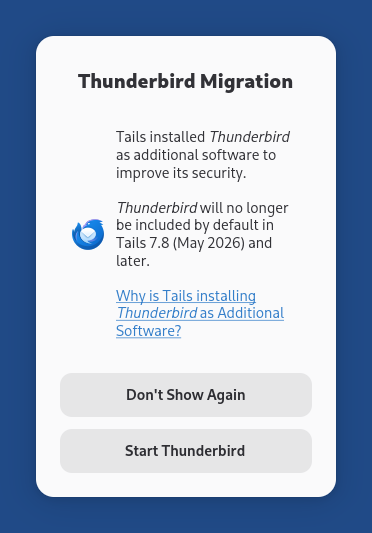
Install Thunderbird as additional software to improve its security, if you have both the Thunderbird Email Client and Additional Software features of the Persistent Storage turned on.
Until Tails 7.5, a new version of Thunderbird was released by Mozilla only a few days after we released a new version of Tails. As a consequence, the version of Thunderbird in Tails was almost always outdated, with known security vulnerabilities.
By installing Thunderbird as additional software, the latest version of Thunderbird is installed automatically from your Persistent Storage each time you start Tails.
If the Thunderbird Migration dialog below appears when you start Thunderbird, it means that Tails successfully installed Thunderbird as additional software.
Include the language pack for Mexican Spanish in Thunderbird in addition to the language pack for Spanish from Spain.
For more details, read our changelog.
Get Tails 7.5
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are available from Tails 7.0 or later to 7.5.
If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a manual upgrade.
To install Tails 7.5 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 7.5 directly:
This release is an emergency release to fix critical security vulnerabilities in the Linux kernel.
Changes and updates
Update the Linux kernel to 6.12.69, which fixes DSA 6126-1, multiple security vulnerabilities that could allow an application in Tails to gain administration privileges.
For example, if an attacker was able to exploit other unknown security vulnerabilities in an application included in Tails, they might then use DSA 6126-1 to take full control of your Tails and deanonymize you.
This attack is very unlikely, but could be performed by a strong attacker, such as a government or a hacking firm. We are not aware of this attack being used in practice.
Update Thunderbird to 140.7.1.
Fixed problems
Fix opening the Wi-Fi settings from the Tor Connection assistant. (#18587)
Fix reopening Electrum when it was not closed cleanly. (#21390)
Fix applying the language saved to the USB stick in the Welcome Screen. (#21383)
For more details, read our changelog.
Get Tails 7.4.2
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are available from Tails 7.0 or later to 7.4.2.
If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a manual upgrade.
To install Tails 7.4.2 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 7.4.2 directly:
This release is an emergency release to fix critical security vulnerabilities in OpenSSL, a network encryption library used by Tor.
Changes and updates
Included software
Update the OpenSSL library to 3.5.4, which fixes DSA 6113-1, a set of vulnerabilities that could be critical. Using this set of vulnerabilities, an malicious Tor relay might be able to deanonymize a Tails user.
We are not aware of these vulnerabilities being exploited in practice.
Update the Tor client to 0.4.8.22.
Update Thunderbird to 140.7.0.
Fixed problems
Fix Gmail authentication in Thunderbird. (#21384)
Add a spinner when opening the Wi-Fi settings from the Tor Connection assistant. (#18594)
For more details, read our changelog.
Known issues
The homepage of Tor Browser incorrectly says you are still using Tails 7.4, even after you have upgraded to 7.4.1. It also links to the release notes for that older version.
If in doubt, to verify that you are using Tails 7.4.1, choose Apps ▸ Tails ▸ About Tails.
Get Tails 7.4.1
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are available from Tails 7.0 or later to 7.4.1.
If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a manual upgrade.
To install Tails 7.4.1 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 7.4.1 directly:
New feature
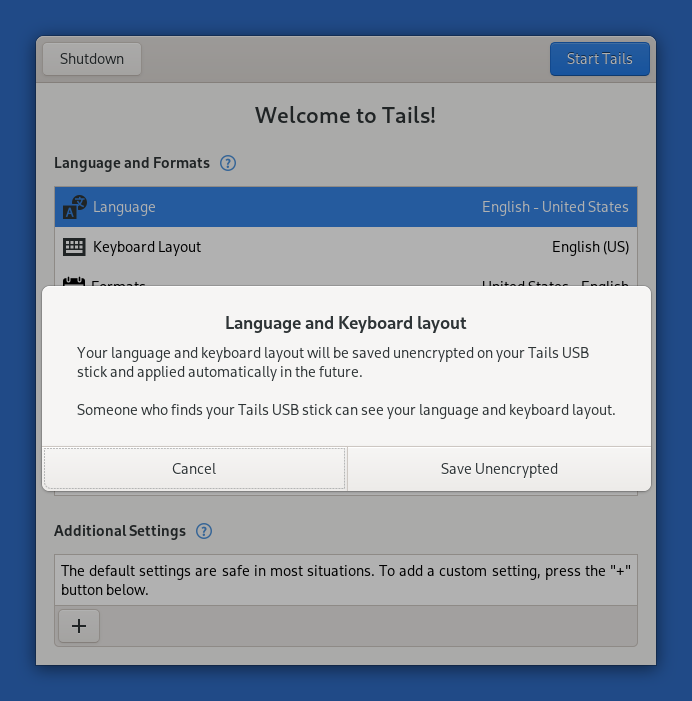
Persistent language and keyboard layout
You can now save your language and keyboard layout from the Welcome Screen to the USB stick. These settings will be applied automatically when restarting Tails.
If you turn on this option, your language and keyboard layout are saved unencrypted on the USB stick to help you type the passphrase of your Persistent Storage more easily.
Changes and updates
Update Tor Browser to 15.0.4.
Update Thunderbird to 140.6.0.
Update the Linux kernel to 6.12.63.
Drop support for BitTorrent download.
With the ongoing transition from BitTorrent v1 to v2, the BitTorrent v1 files that we provided until now can become a security concern. We don't think that updating to BitTorrent v2 is worth the extra migration and maintenance cost for our team.
Direct download from one of our mirrors is usually faster.
Fixed problems
Fix opening .gpg encrypted files in Kleopatra when double-clicking or selecting Open with Kleopatra from the shortcut menu. (#21281)
Fix the desktop crashing when unlocking VeraCrypt volumes with a wrong password. (#21286)
Use 24-hour time format consistently in the top navigation bar and the lock screen. (#21310)
For more details, read our changelog.
Get Tails 7.4
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are available from Tails 7.0 or later to 7.4.
If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a manual upgrade.
To install Tails 7.4 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 7.4 directly:
Today, we are releasing 7.3.1 instead of 7.3 because a security vulnerability was fixed in a software library included in Tails while we were preparing 7.3. We started the release process again to include this fix.
Changes and updates
For more details, read our changelog.
Get Tails 7.3.1
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are available from Tails 7.0 or later to 7.3.1.
If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a manual upgrade.
To install Tails 7.3.1 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 7.3.1 directly:
Changes and updates
Update Tor Browser to 15.0.1.
Tor Browser 15.0 is based on Firefox 140 and inherits from it several new features that are particularly useful if you use many tabs:
- Vertical tabs
- Tab groups
- New address bar with improved search
Update Thunderbird to 140.4.0.
Update the Linux kernel to 6.12.57.
Remove Root Console.
To open a root console, you can execute the following command in a Console.
sudo -i
Show Don't ask again notifications only after the clock has been synchronized.
Fixed problems
- Disable connections that Thunderbird was making to telemetry services run by Mozilla. (#21275)
For more details, read our changelog.
Get Tails 7.2
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are available from Tails 7.0 or later to 7.2.
If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a manual upgrade.
To install Tails 7.2 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 7.2 directly:
This year we are calling to FREE THE INTERNET! By supporting Tor, your donation will help break the chains of censorship and surveillance. If you give now during the campaign, your donation will be matched by our supporters at Power Up Privacy. This means a $25 donation will have a $50 impact — and all donations over $25 will qualify you for fun Tor merchandise. 👀
At the Tor Project, along with our incredible community of supporters, we're not just envisioning a free internet — we're building it:
In countries like Turkmenistan where access to information is tightly controlled, Turkmen.news trusts Tor to provide safe access to the free internet where it once did not exist.
Freedom of the Press Foundation uses Tor as the backbone of SecureDrop, a tool that allows journalists and sources to communicate freely without fear of retaliation or exposure.
In Russia and Egypt, where authorities often block encrypted tools to control communications, individuals use Tor Browser to access encrypted email services like Tuta Mail to freely communicate.
Tor is a building block for a free internet, and it takes our collective efforts to improve and amplify it. That’s why during the next three months, the Tor Project will be holding a fundraising campaign during which we ask for your support to advance digital freedom.
To learn more about how Tor is freeing the internet from surveillance and censorship, and how we are putting charitable donations to work, please tune into our annual State of the Onion virtual event to learn more. Save these dates and make your donation today!
Upcoming events
State of the Onion – the Tor Project (Wednesday, November 12)
The State of the Onion is the Tor Project's annual virtual event where we share updates from the Tor Project and the Tor community. The event on November 12 will focus on the Tor Project and the organization’s work.
📺 Stream live on our YouTube channel
State of the Onion – Community (Wednesday, December 10)
The State of the Onion is the Tor Project's annual virtual event where we share updates from the Tor Project and the Tor community. The event on December 10 will be a special day celebrating the UN’s adoption and proclamation of the Universal Declaration of Human Rights (UDHR) in 1948 as well.
📺 Stream live on our YouTube channel
Ways to get involved
Make a donation: Donate through our website (or any other method listed on our FAQ) and your donation will be matched, 1:1, up to $250,000.
Ask the company you work for if they will match your donation: Many corporations will match their employees’ donations to charitable organizations. Ask at work if your company will match your gift.
Share on social media: Let the people in your networks know that all donations to the Tor Project are currently being matched. You can easily share a post from our social channels: Mastodon, Bluesky, X, and more.
Subscribe to Tor News: No ads. No tracking. Just low-traffic Tor updates via email.
Thank you for supporting a free internet.
Changes and updates
Change the home page of Tor Browser in Tails to an offline page, very similar to the home page of Tor Browser outside of Tails, instead of an online page from our website.
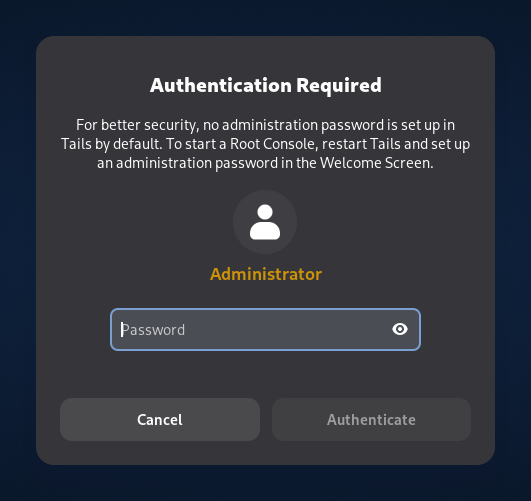
Improve the message when an administration password is required to open an application but no administration password was set in the Welcome Screen.
Update Tor Browser to 14.5.8.
Update the Tor client to 0.4.8.19.
Update Thunderbird to 140.3.0.
Remove the package
ifupdown.
Fixed problems
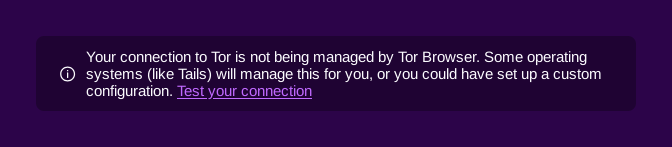
Hide the message "Your connection to Tor is not being managed by Tor Browser" in new tabs of Tor Browser. (#21215)
For more details, read our changelog.
Get Tails 7.1
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are available from Tails 7.0 or later to 7.1.
If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a manual upgrade.
To install Tails 7.1 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 7.1 directly:
We are very excited to present you Tails 7.0, the first version of Tails based on Debian 13 (Trixie) and GNOME 48 (Bengaluru). Tails 7.0 brings new versions of many applications included in Tails.
Dedication
Tails 7.0 is dedicated to the memory of Lunar (1982–2024). Lunar was a traveling companion for Tails, a Tor volunteer, Free Software hacker, and community organizer.
Lunar has always been by our side throughout Tails' history. From the first baby steps of the project that eventually became Tails, to the merge with Tor, he's provided sensible technical suggestions, out-of-the-box product design ideas, outreach support, and caring organizational advice.
Outside of Tor, Lunar worked on highly successful Free Software projects such as the Debian project, the Linux distribution on which Tails is based, and the Reproducible Builds project, which helps us verify the integrity of Tails releases.
Lunar will be deeply missed, both in our community and in the many other communities he participated in.
See also what other projects have written about Lunar.
Changes and updates
Faster startup
Tails 7.0 starts 10–15 seconds faster on most computers.
We achieve this by changing the compression algorithm of the Tails USB and ISO
images from xz to zstd. As a consequence, the image is 10% bigger than it
would be with the previous algorithm.
While testing this change, we noticed that Tails on USB sticks of poor quality can also start 20 seconds slower than on quality USB sticks.
If you are in a place where counterfeit electronics are common, we recommend that you buy your USB stick from an international supermarket chain, which should have a more reliable supply chain.
Included software
Replace GNOME Terminal with GNOME Console.
Replace GNOME Image Viewer with GNOME Loupe.
Update Tor Browser to 14.5.7.
Update the Tor client to 0.4.8.17.
Update Thunderbird to 128.14.0esr.
Update Electrum from 4.3.4 to 4.5.8.
Update OnionShare from 2.6.2 to 2.6.3.
Update KeePassXC from 2.7.4 to 2.7.10.
Update Kleopatra from 4:22.12 to 4:24.12
Update Inkscape from 1.2.2 to 1.4.
Update GIMP from 2.10.34 to 3.0.4.
Update Audacity from 3.2.4 to 3.7.3.
Update Text Editor from 43.2 to 48.3.
Update Document Scanner from 42.5 to 46.0.
Changes in GNOME
Many sections of the Settings utility have been redesigned, for example Accessibility, Sound, and Mouse & Keyboard in GNOME 44
Accessibility settings also include new accessibility features, such as Overamplication and Always Show Scrollbars.
The Activities button has been replaced with a dynamic workspace indicator in GNOME 45.
The Screen Reader has been improved in different ways, for example, with better table navigation and a sleep mode in GNOME 46.
A new option to preserve battery health is available in the power settings in GNOME 48.
Removals
Remove the Places menu.
You can access the same shortcuts from the sidebar of the Files browser.
Remove Kleopatra from the Favorites menu.
To start Kleopatra, choose Apps ▸ Accessories ▸ Kleopatra.
Remove
unar.The File Roller utility still opens most RAR archives.
Remove the
aircrack-ngpackage.You can still install
aircrack-ngusing the Additional Software feature.Remove the Power Statistics utility.
Remove the
sqpackage.Remove the obsolete Network Connection option from the Welcome Screen.
Hardware support
Update the Linux kernel to 6.12.43.
This improves support for newer hardware: graphics, Wi-Fi, and so on.
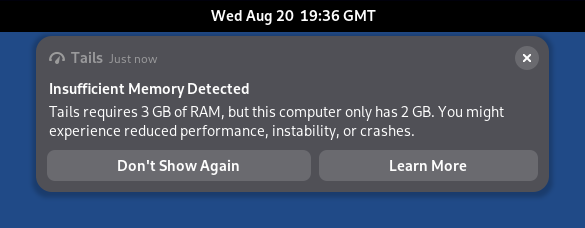
Increase the memory requirements from 2 GB of RAM to 3 GB. (#21114)
Tails 7.0 displays a notification when the RAM requirements are not met.
We estimate that less than 2% of users are affected.
Fixed problems
- Fix selecting the correct keyboard for certain languages. (#12638)
For more details, read our changelog.
Get Tails 7.0
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are only available from Tails 7.0~rc1 and 7.0~rc2 to 7.0.
All other users have to do a manual upgrade.
To install Tails 7.0 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 7.0 directly:
Changes and updates
Fixed problems
For more details, read our changelog.
Get Tails 6.19
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are available from Tails 6.0 or later to 6.19.
If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a manual upgrade.
To install Tails 6.19 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 6.19 directly: